If you have a secure combination of username and password to log in to your server (or VM), brute-force attacks are unlikely to succeed. If you use a bad/insecure password, you will be hacked in a whiff. If your password is even on the top 10k list of reused passwords, you're likely to be hacked sooner or later.
I believe my choice of username and password is secure enough to survive RDP brute force attacks for the time being, but I still find it annoying that these kids are trying to break into my server so I wanted to have a way to block them.
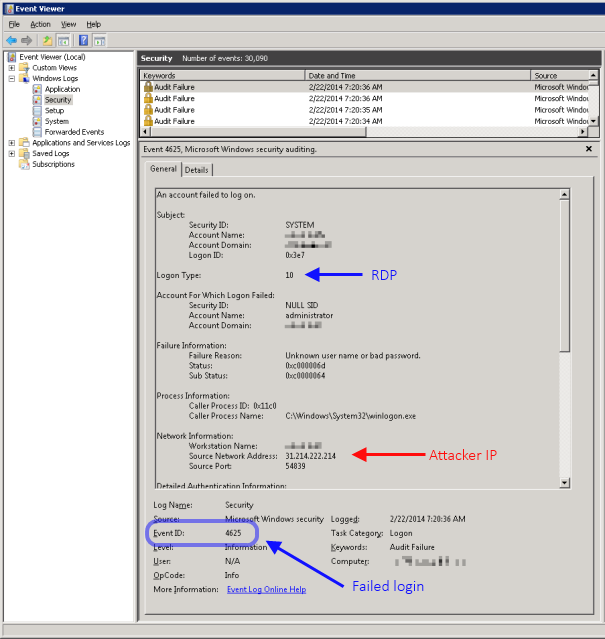
Signs of a RDP brute-force attack
Whenever a server is under attack, it will log large amounts of Audit Failure events with event id 4625 in the Security event log. Each entry contain details about the login attempt, including the remote IP address of the attacker. It looks something like this on a Windows 2008 R2 server:
Blocking attackers
Since the event log entries contain the attacker's IP address, they can of course be blocked by adding them to a firewall rule. Naturally, noone would want to do that by hand, as it would be time consuming and most likely too late (the attack has either failed and the attacker moved on, or been successful and the server compromised).
Instead, I updated and repurposed a service I wrote back in the days of the ASP.NET POET vulnerability. The service simply monitors the event log for a pre-defined type of events (in this case the above mentioned Audit Failures), and if it detects too many originating from the same source IP within an hour it adds the originating IP to a firewall block rule, and optionally sends an email alert to the server admin.
In short, the service creates an event log listener and will listen for failed login attempt event log entries. If the same IP address has more than a configurable (default 10) number of failed logins within an hour, it is added to a firewall block rule in the Windows firewall. Warning: this will of course also block legitimate users if they have forgotten their username and/or password and try to log in repeatedly with invalid credentials.
The service also looks for signs of a distributed attack; if failed logins from multiple IP addresses exceed a pre-defined threshold (default 50) within an hour, it sends an email notification to the server admin.
Download
I have made a beta version of the RDP blocker service available for download for anyone brave enough to test it. Binaries for the compiled version is available here: HuagatiRDPBruteForceBlockerService_release_v112.zip, and the source code is available here: HuagatiRDPBruteForceBlockerService_source_v112.zip
Disclaimer: Use at your own risk. If used incorrectly, or if there is a bug or flaw I didn't think of, this service can potentially lock you out of your server permanently and/or prevent legitimate users from accessing it. Do not use on vital/important/production systems. Any use (or misuse) is your own responsibility. No support provided. Batteries not included. Don't use this service if you don't know what you are doing, and even if you do it has not yet been tested enough to be deemed safe. I have only tested this service on a Windows 2008 R2 system with US-English Windows. Using it on other versions of Windows and/or other localized variants may have unintended consequences. Depending on network configuration and/or firewalls in front of your server, *all* external traffic may appear to come from the same (internal NATed) IP address to your server. If this is the case, the service will block all traffic to your server.
Installing and configuring the service
The following steps are required to install this service:
- Download the service onto the server where you are going to install it.
- Right-click on the zip file, go to Properties, click on the "Unblock" button.
- Unzip the contents into a folder where you want to install the service.
- Run installutil /i HuagatiRDPBruteForceBlockerService.exe to register the service in the Windows service configuration. The installer will prompt for the username and password that the service will run under, this account must have administrative privileges to be able to create firewall blocking rules.
Installutil is part of the .net framework and can usually be found under C:\windows\Microsoft.NET\Framework\v4.0.30319. - Edit HuagatiRDPBruteForceBlockerService.exe.config using your favorite text editor. Update all relevant configuration options* to match your system/environment.
- Start the service from the windows service manager.
* = The configuration file contain several configurable parts. The following describes the important ones that you need to, or may want to update:
SMTP settings
configuration/system.net/mailSettings - this section contains the details needed by the service to send email via your SMTP server. You need to update (at a minimum) the host name, user name, and password used to authenticate against your SMTP server. Additional details about available configuration options are available here.
Service app settings
configuration/applicationSettings/HuagatiRDPBruteForceBlockerService.Properties.Settings - this section contains the settings that controls the configurable parts of the service's behavior.
The following describes each of those settings:
- MaxFailedLoginsPerIP - numeric value, number of failed login attempts allowed for one individual IP address within an hour.
- UseFirewallBlock - boolean (True/False), controls if firewall blocking is enabled. If you want to run the service in "warnings only" mode where it sends email alerts without blocking potential attackers, set this to false.
- SendEmailNotification - boolean (True/False), controls if email notifications are enabled. If you do not want the service to send email alerts/notifications when detecting potential brute-force attacks, change this settings to false.
- EmailNotificationFrom - email address that will appear as the sender for all notification emails sent from the service.
- EmailNotificationTo - email address that any email notifications will be sent to.
- WhiteList - comma separated list of IP addresses that the service will not attempt to block/blacklist. Add your own static IPs to this list to avoid getting blocked if you mistype your password.
- EventLogName - the name of the security event log on the local system.
- EventLogQuery - event log listener query used for finding failed login attempts in the Security event log.
- IPMatchRegEx - regex used to find the IP address of the attacker in the event log entry.
- DistributedAttackWarningThreshold - threshold for number of failed login attempts allowed from multiple IP addresses within an hour before an alert is sent for a potential distributed attack.
Again, feel free to grab the blocker service from the download links, but use at your own risk. If you have any comments/feedback/questions, please feel free to post in the comments section below.



nice little tool :)
ReplyDeleteSomethings that could improve your programm would be, creating one firewall rule and add all the ip addresses to this rule. Don't create for each blocked ip a separated rule.